The time has come for technocracy to wrap its shiny tentacles around the human race. The long incubation period in buddy masks has slipped to reveal the pǝʇɹǝʌuᴉ, distorted, authoritarian face of a monster for the ages. Unfortunately, the tech wasn’t *quite* ready, so the canoe got flipped. A few missteps later & the push back is just getting started. This first post will cover some basic concepts, but we will dig deep & get specific later on.
Own Goals
Their real goals of complete control have been revealed. Goals which have, by the way, been written about for centuries. Control of the population, remotely by the few. If you build the sharpest axe around, be very careful not to cut your own foot off. Be even more careful the axe doesn’t get taken from you. Skinny bicep, twitchy authoritarians who probably should have worked out harder. They will need it to face the multi-hydra tsunami that is an angry & informed population.
I Spy, but Why?
The spy grid that was built for controlling the people is now in the hands of President Donald J. Trump. How you feel about that depends on your position & perspective. How we feel has never changed, no one has the right to censor others. The spy grid plan was flawed & next the builders get owned as the tools of control are welded against those who wished to monopolize its power.

Understanding Why
So why do these companies want to censor & spy on everyone so badly? Originally, the plan was to build a control grid by giving away as much as possible & collecting massive amounts of data.
We’ll refer to this as Trojan Tech. Once controlled, the goal was to strip almost everyone of their wealth & power, except a few connected people across different industries. We’ll refer to this technique as Capstoning. Now that their power has slipped, their goal is regaining control to bury the massive amount of serious crimes they committed among the way. There was no need for clean up, as they expected to remain in control.

Trojan Tech
It is pretty easy to understand. A well connected, well funded company with the goal of monopolizing a niche or industry, by undercutting existing competitors. They used to be called predators. Many still are. With a combination of capstoning, financing & trojan tech, mediocre talent/ideas are able to make it to the top.
This happens across many industries. Once trojan tech gets entrenched, it becomes very difficult to remove. Its purpose is to build up data, moats & all kinds of defensive rent seeking. You can see it in tech startup funding, the Varsity Blues scandal & many other aspects of life. Expensive schools give scholarships to poor kids so that their average numbers are higher.
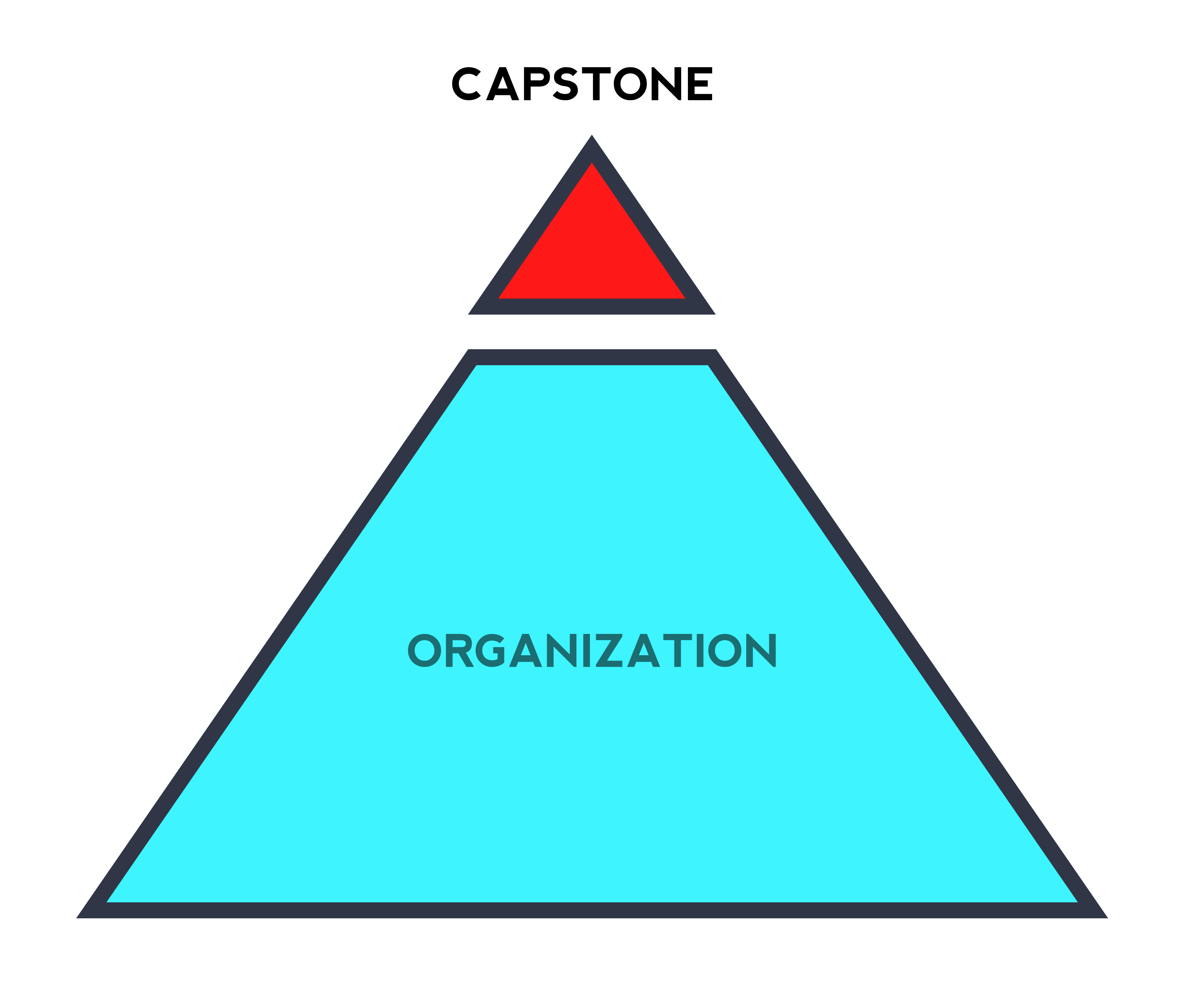
Capstoning
This technique requires focus on the situation & people in control. So the exact method of execution may vary, but the goal is the same; controlling the levers of power. From inception, an organization (movement or business) tries to be on trend. They copy something people like & recreate their own version.
Then they use their resources to ‘take the lead’. Key methods for gaining control include buying/compromising/replacing competition staff & execs (Martin Eberheard – Inventor of the Tesla Roadster); lateral capstoning from other industries (The MIT designer with the Brad Pitt boyfriend); halo transfer (Michael Jackson’s exclusive on Oprah Winfrey’s show); idol pushing “Picasso is the greatest” – Rubens; defaulting (Search boxes that default to Google).
New Goals
A combination of finance, trojan tech & capstoning allowed a monolithic group of individuals to capture many industries, powerful positions & influence vast swathes of public opinion. Often via celebrity & pillar capstoning. Now however, they need to censor anyone going against their plan. To wrestle control back from Donald Trump. The 2016 US election was not about politics as usual, it was about who got the keys to the kingdom [grid].

Ownership & Value
The goal of big tech is to strip your value from you, for profit & control. If you are using technology, especially if it’s for your livelihood, careful attention should be paid to how much of the value chain you can retain. The more you retain vs tech, the more likely you will be able to make your own decisions.
Preparation
There are many things you can do to prepare, help others & prevent further technocratic invasion. Take stuff offline, meet in real life, plan ahead, create content, schedule stuff for when you are busy, build up a rainy-day fund, teach people what you know.
Renting vs Owning
Any content you create is subject to the terms & conditions you agree to on the platform where you publish. Usually this means giving up your rights, IP & ability to start legal proceedings. Publishing on your properties means you own the content & can do what you want with it. While it does present a couple of issues, including set up, cost & ability to engage with ‘the conversation’, there are ways to resolve this.
Whose Rules?
Never play a game without knowing the rules, it is not likely you are going to do well. Try to adapt the rules to suit you better, bend theirs. Technology is brittle, whereever you bend it, it tends to snap. Often that is true of its owners too.

Privacy Protections
Privacy has gone from being a desirable feature to a core selling point. Five years ago clients were reluctant to spend extra on advanced security & privacy measures, now it is central to growth. Whole industries, businesses & reputations are hockey sticking (growing fast, up to the right).
No Clouding
Friends don’t store friend’s data in the cloud. When you store your contacts in the cloud, you violate the privacy of your friends. Most address books come with an offline mode. If you can live without using cloud services, then in general it is better not to. For most services there are reasonable ways around.
Every movement should be available on video, every email and message logged and read, and every conversation recorded. Even the most top secret and sensitive state negotiations should be watched by duly vetted, randomized—and constantly monitored—professional monitors. +
Dr. Lawrence M. Sanger. Philosopher & Founder of Wikipedia.
Browsers
Most browsers violate your privacy from first install. As web designers, this is especially frustrating & we know who the exact people responsible are.
Over time software & staff change, so there is never a permanent solution. In general we recommend reviewing what experts of all sides are saying about the browser you want to use.
Avoid Chrome, IE, Opera & use a browser from a different provider. The stated goal of Brave is to protect your privacy. It is from Silicon Valley, but we can’t hold that against them, too much. Check out our giant list of web browsers for other options.
Use Web, Not Apps
In general browsers are more sandboxed than other applications. Apps tend to have a lot of datelining going on under the surface. Using a web browser & web versions of the applications you like is often better. We make a lot of apps, but at this point even we have to say this.
Crypto, Blockchain & Bitcoin
None of these technologies are particularly private. It’s better than a credit card for privacy, but in reality the majority of people who shill are loaded up, have little tech experience (mostly e-finance) & fall deep into utopian fallacies. Cash is the most private still. Only a tiny fraction could PR the repos.

Forward Actions
Be proactive & take back as much as you can. By starving them of their information fix, you starve them of the ability to make good decisions. In this scenario, any small improvement helps. It is not a zero-sum game.
Block Everything
A lot of people will try to convince you that blocking ads is bad, feel free to ignore them. Some silly nonsense about how “creators starve”, but that was never how the system worked. If you want to help creators, good. If you don’t, that is your prerogative.
The ethical debate is faux. Ads are a form of forced platforming & usually privacy violators. Not all ad blocks are created equal. Some ad block companies are collecting your data. Most of the ad business is Alphabet (Google) & Facebook anyway.
Router Block
Use router blocking & ad blocking. Some blocking companies are trojans, so do your research. Blocking will keep moving lower down the stack until privacy is reclaimed. Ad/tech companies will try to make you feel bad, but they are the reason & the violators, so pay no mind.
Atomization
Spilt everything over as many places as possible. Break habits of going back to the same place & doing the same things. Break up your news, chats, social & logins. Use different identities, profiles, browsers, machines, connections, operating systems & hardware.
Meme Warfare
Memes are an art form & a powerful tool. Plus meme warfare is one of the most fun parts of the battle. Memes are used to circumvent various automated editorial control points of social media sites. So go ahead, make & share more. Mostly you’ll find you are less original or funny than you hoped. Although if you make some good ones, the reward is great.
Defaulting
Use one company for everything, pay them. it reduces the number of 3rd parties who have access to your information. Apple’s ecosystem & direction is a good example of this. Apple is not a good company & it’s top executives are bad [apples].
De-Embedding
Remove/don’t use embedded fonts (download & self-host), embedded video or scripts (link/use an image with popup). Every embed is a point of data leak.
Fuzzy Logic
The goal of using fuzzy logic is to warp the data you are exposing. Mix up your data by swapping devices with people, leaving them at home, using different devices & searching for unusual stuff (there are tools to do this automatically).
Logins
Facial & biometric recognition including Face ID & Touch ID are unwise to use as they can pass on data that confirms it is you using the device. With a password, it could (in theory) be anyone accessing your devices.
Holding Back
Hold stuff back, especially if it is a heavy counterpunch. Set traps & when the hit pieces, reputation attacks come, drop it on them. Then drop more. Keep dropping until they realize, they stepped into a minefield. This goes back to preparation.
Punch Sideways
When attacked by the borg, turn sideways & target someone/something else. Drag them in, Make them defend their position. Keep doing this. Don’t scream at giant corporations & organizations, side punch until it becomes everyone’s problem.
Google just announced that in Q2 of 2019, it removed 500 million comments, 100,000+ videos, & 17,000+ channels from You Tube for “hate speech”. But who gave this private company the right to define “hate speech” & to decide what the world can or can not see?
Dr. Robert Epstein. Harvard Professor, author, researcher & former editor-in-chief of Psychology Today.
E-mail has many benefits & it is already decentralized to some degree. It is generally not private, but is useful as a form of communication. You can easily host your own. Stop using Gmail & Hotmail. Turn off 3rd party script tracking. Use IMAP or POP & clear your servers.
Disclosure
This site is sometimes (currently) hosted on Bezos trojan hosting. Happy for suggestions on good (principles & quality) hosts. Willingly disclose where your tech is less likely to be perfect.

Build > Speak
The constant shouting at big brands & companies on social media does very little to change anything. Professionals on the other side are getting paid to deal with it. Once in a while it makes a difference, but there are better ways to speed up progress.
Focus on people, not brands. Find their key players & expose, focus an audience spotlight on them.
Make Things
The very best way to circumvent other people’s plans is to make things. The more you make & the more diverse, the better tomorrow will be. Once the corrupt have been deboarded, there will be a need for new tech. Those who start now will be prepared at the right time to benefit.
Data Blackholes
Create silos, incompatible information & data blackholes everywhere you go. Delete tweets, delete accounts, ask for stuff to be removed, use broken links & do what you want. Not what the industry pushes out as the correct way.
Forming Connections
It’s worth getting your numbers up a bit on social accounts, as people believe it matters (it depends). Although more important is credible, genuine connections & a provenance of being right/on the right side/well-meaning/kind-hearted or of good character. Avoid people who signal too much, usually they are projecting something. Genuinely virtuous people tend to be working, tired or thinking about what else they can do. Not what face they can present in public.
Communications
Knowing how communications work via technology is important in preventing yourself ending up in a Gmail drafts situation. (Stop using Gmail drafts to ‘secretly’ communicate. It’s not secret. Looking at you, people who should know better.)
Social Media
Diversify your social media. You will probably get better results on other sites. Try sites that promise freedom of speech. You can check out our giant list of social networks for more ideas.
Private Chat
Use private, encrypted chat apps to communicate. Switch it up, don’t give everything to one supplier & use lots. Try to find good suppliers & avoid the big ones.

Improved Comms
Finding better ways to communicate helps you circumvent gatekeepers, censors & algorithms. The key to being good at getting around the system is to prepare & practice. Prepare by setting up stuff (accounts, sites, connections) you can use later & practice (publishing, getting exposure).
Language Evolution
Continuously evolve your language & ability to communicate. Use slang, mistakes, typos, bad grammar, similes, metaphors, language deconstruction, reconstruction & any other twisting you can. It takes time to develop monitoring mechanisms, so there is a lag between what you can say & what can be picked up by the machines.
Conversation Atomization
Split your conversations over different platforms. Switch it up & make it hard to follow, leak or analyze in detail. Put stuff in screenshots, use private chats, make memes, use multiple accounts & anything else you can to turn your communications into a mist form.
Fighting Back
Don’t be afraid to fight back, they have been fighting you for years & winning. However, the tide has turned & the numbers are not in their favor at all. Across all mediums right now, the authoritarians are stagnating or losing traffic. Even if their numbers look big (often fake) their engagement is almost nonexistent.
Profitable Resistance
The numbers are now big enough & the value is there to turn the fight into a profitable business or brand. In fact, there is more growth & engagement than most other areas. Build services that support liberty, people’s rights & help inform others.
How to Check for Censorship
Mostly don’t waste your time. Create better stuff, the best stuff breaks the hardest filters. Keep working it. Connect with real people & form real groups, use those to climb over basic algorithms.
Censor the Censors
Block them, shut them down, fight back, brigade them, troll them. The more they tell you what to do, the more you should push back hard & fast. They are not at the point they can control the narrative any longer.

New Kings & Queens
New kings & queens are being anointed daily, as the people move from one world view to a new one. People will tell you there is no need for leaders, strong voices & heroes, but that is not true. Not everyone can or wants to lead, but will help in more ways than imaginable. A hero is not an idol & should be judged on their work/actons.
Support New Stuff
Smaller, newer players are often better to support, but not always. Many are funded & controlled by larger entities. A large selection of competing services will produce a higher standard & reduce the chance of monopolization.
Exposure
Follow people who are fighting, exposing or rebuilding the systems. Support them. Exposure is the thing that the technocrat ruling class are terrified of. They have never had to deal with substantial negative press before & it shows. Their actions make them look worse.

Recommended Movies
Technocrats have always enjoyed seeing their visions on the big (& little) screen. The ‘halo’ glow from Hollywood is desirable amongst the tech crowd. A lot of movies & TV are focused on Overton window (or creeping normality) shifting, thought experiments & future-past timelining. It’s also good for capstoning.
Metropolis
The original 1929 robot future vision for the big screen by Fritz Lang. This occult freakshow should show you just how far back & high up these weirdos go. Oddbods.
The Matrix
The concepts are straightforward to grasp, but what should be understood is that it is part of a plan, not just a movie. Merovingian, The One, Oracle, Nebuchadnezzar, Morpheus, blah blah. This is all just occult worship.
2001 A Space Odyssey & Eyes Wide Shut
Eyes Wide Shut shows the kind of things technocrats get up to when they are not salivating over your resources.
Demolition Man
Demolition Man is a look at an ‘improved society’ via technocracy & total control. Picture yourself as the sewer people, not protagonist or villain. In this movie, you are eating rat underground.
Idiocracy (Wall-E)
Dumb pig-people (us) have ruined earth & it needs repaired by the Titans (elites like post transformation Jack-Brzezinski-Kissenger, the 1% centipede).
Hunger Games/Running Man/The Purge/Predator/Ratrace
These are basically the same movie. Spoilt, inbred Hapsburgs play games with people’s lives for entertainment-control. They always end up looking like vampires in sparkly outfits [for some reason]. A losers view of winning.
Inception/Truman Show
Satirical looks at how people are trapped inside of mental bubbles created by gaslighting structural systems whose goal is to distract & delude. Laughing at you, not with you.
Elysium
Breakaway elite civilisation. One side works in bad conditions. The other side lives away in space, in a theoretical paradise. Picture all your favorite stars & celebs up there while you do backbreaking work for 12+ hours a day. Yes, Damon is a bad guy playing a nice guy in most movies, except Dogma. ?

Recommended Authors
The best way to understand the plan is to study those whose idea it was (this phase at least). Most of the really valuable information exists in mainstream culture rather than in the expected places. We call this Truffle Pigging – where you, the pig, are searching for valuable nuggets in a forest that is just the farmer’s land. You never find answers, you don’t get the truffles & you never leave the farm.
Arthur C. Clarke
Arthur C. Clarke invented the geostationary orbiting satellite & laid out a plan for the technocracy. Wrote & advised on Kubrick’s 2001 A Space Oddessy. Read Hammer of God, The Trigger, Rendevouz with Rama & watch all the old videos.
Michael Crichton
Famous for Jurassic Park (de-extinction), all of Michael Crichton’s books are focused on revealing hidden knowledge & plans, dressed as something else. Next (DNA ownership & transhumanism), Prey (Nano/micro tech), The Terminal Man (mind control via technology), Rising Sun (Asia’s rise as a global power & deepfakes).
George Orwell (Eric Arthur Blair)
Most people mistake Orwell’s writings to be warnings of a dystopian future. In reality, it is the worship & idolization of a future where most people live under those circumstances. Animal farm is about self-governance. 1984 is life for resistors. The Road to Wigan Pier is to taste suffering & depravity. Orwell was never a rebel, he was the slowly-disclosing mouthpiece of the system.
Tom Clancy & Steve Pieczniek
NetForce is a early look at digital warfare in the cyber domain, by experts. Steve’s coup video is pretty eye opening too.
Aldous Huxley
Orwell’s mentor/teacher, Huxley’s plan is both earlier than Orwell’s & describes what life would be like for those who comply [those who don’t fight]. Seems boring to us, how about Huxley, Atwood & Orwell take a vacation at Her Majesty’s Pleasure for eternity. You can add Warner Brother’s V for Vendetta to that too.

Extended Reading
Dig deeper & learn more about how to control your digital lifestyle, take back your freedoms. Learn why, how & what is going on.
- Morals & Dogma – Albert Pike
- Propaganda – Edward Bernays
- Crystallizing Public Opinion – Edward Bernays
- The Secret Teaching of All Ages – Manly P. Hall
- EpsteinTweetStorm.com – Dr. R. Epstein
- States Launch Antitrust
- The Grand Cheesboard – Zbigniew Brzezinski
- No Logo – Naomi Klein
- The Shock Doctrine – Naomi Klein
Your info will only be used for comments. No Gmail.